Deepfakes, the Simplicity of Creation and Associated Security Risks
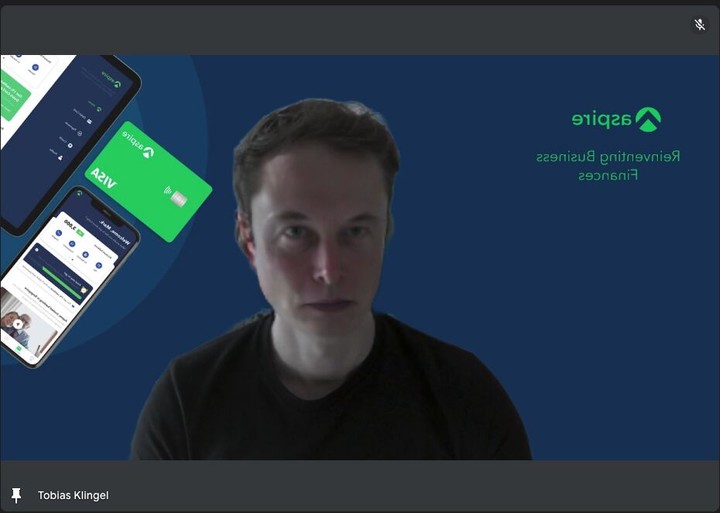 Deepfake demonstration in a live meeting scenario.
Deepfake demonstration in a live meeting scenario.
A Technical Deep Dive into the World of Deepfakes
Advances in AI have made it possible to create deepfakes – highly realistic fake videos or audio – with increasing ease. This article breaks down the technical process of creating deepfakes, examines the tools and skill required, and discusses the significant security risks they pose.
How Deepfakes Are Created: A Technical Breakdown
Deepfakes are generated by leveraging neural networks, specifically autoencoders and generative adversarial networks (GANs), to swap one person’s face with another’s. The process generally involves:
-
Data Collection:
- Gather hundreds of images or video frames of both the source and target faces.
- Use facial detection algorithms to extract and align faces from the source footage.
-
Model Training:
- Employ deep learning models (e.g., variational autoencoders) to learn facial features.
- Train two models – one for the source and one for the target – then combine them to map facial expressions from one face to the other.
- Training is compute-intensive, often performed on GPUs and taking several hours to days.
-
Face Swap & Synthesis:
- Pass the source actor’s image through the trained encoder and decode with the target’s decoder to generate the target’s face with corresponding expressions.
- Blend the generated face into the original video, using post-processing techniques for color correction and artifact removal.
-
Audio (Optional):
- Use AI voice synthesis models to clone the target’s voice, synchronizing the audio with the generated video via lip-sync algorithms like Wav2Lip.
Tools such as DeepFaceLab, FaceSwap, and DeepFaceLive (for real-time applications) utilize Python-based scripts and popular frameworks like TensorFlow or PyTorch to streamline this workflow. Additionally, OBS Studio is often employed to integrate the output into live streams or meetings.
Skill Level and Evolving Accessibility
Originally, creating a convincing deepfake required significant expertise in machine learning and programming. Over time, the technology has evolved:
- Early Tools:
Early adopters developed custom Python scripts and trained models from scratch. - User-Friendly Applications:
Tools like FakeApp and open-source projects such as DeepFaceLab and FaceSwap have lowered the technical barrier by providing GUIs and comprehensive documentation. - Real-Time and Mobile Solutions:
Applications like DeepFaceLive enable live face swaps, while mobile apps such as Reface allow casual users to generate basic deepfakes with minimal effort.
These developments have made it possible for even less experienced users to create and deploy deepfakes, increasing both the potential for creative applications and the risk of malicious use.
Deepfake Creation Tools Comparison
| Tool | Ease of Use | Realism | Availability |
|---|---|---|---|
| DeepFaceLab | High complexity – requires ML expertise, a dedicated GPU, and command-line operations. | Very High – capable of producing smooth, high-fidelity deepfakes with sufficient training. | Open-source (free) – Available on GitHub. |
| FaceSwap | Moderate – offers a more user-friendly GUI and extensive documentation compared to DeepFaceLab. | High – delivers comparable quality to DeepFaceLab with less complexity. | Open-source (free) – Community-driven on GitHub. |
| DeepFaceLive | Moderate – designed for real-time applications but still requires a decent GPU and setup. | Medium – lower resolution and minor artifacts due to real-time processing constraints. | Open-source (free) – Integrates with OBS Studio. |
| Reface (mobile app) | Very Easy – no technical skills required; simple upload and selection process. | Medium – produces fun and recognizable results, but limited to short clips with reduced resolution. | Proprietary – Freemium model with watermarked outputs. |
| Deepfakes Web | Easy – no coding required; cloud-based service handles training and generation. | High – quality varies with training time and data provided, capable of producing realistic swaps. | Commercial – Subscription or pay-per-use service. |
Table: Comparison of deepfake creation tools based on ease of use, realism, and availability.
Security Risks and Threats Posed by Deepfakes
Deepfakes present several significant security risks:
-
Identity Fraud & Impersonation:
Deepfakes can convincingly impersonate individuals, enabling fraudulent transactions. For example, a deepfake voice was once used to trick a company director into transferring funds based on a simulated CEO request. -
Misinformation & Political Manipulation:
Deepfakes can spread disinformation and manipulate public opinion by fabricating statements from political figures. A notorious example involved a fabricated video of a national leader allegedly urging surrender, which was quickly debunked. -
Corporate Security Threats:
Authentication systems based on biometrics are vulnerable. Tests have shown that deepfakes can bypass facial recognition systems, posing risks to secure access in financial and corporate environments. -
Personal Harassment & Defamation:
A disturbing majority of deepfakes target private individuals, particularly in non-consensual explicit content, leading to severe personal and reputational harm. -
Undermining Trust in Media:
The ability to fabricate convincing audio and video undermines public trust in digital media and complicates legal and journalistic verification processes.
Detection and Mitigation Strategies
To counter the threat posed by deepfakes, several detection and mitigation strategies are being developed:
-
AI-Powered Detection:
Utilize convolutional neural networks (CNNs) to detect subtle artifacts such as inconsistent blinking, facial misalignments, or unnatural skin textures. Initiatives like the Deepfake Detection Challenge have spurred significant advancements in this area. -
Digital Watermarking & Provenance Tracking:
Embed cryptographic signatures or watermarks in original media files to enable authentication. Standards such as C2PA are being developed to ensure that digital media can be reliably traced back to its source. -
Policy and Best Practices:
Implement organizational protocols for identity verification and multi-factor authentication to mitigate the risk of deepfake-enabled fraud. Educating employees about deepfake threats is crucial. -
Emerging Technologies:
Explore experimental approaches like blockchain-based media logs and anti-deepfake perturbation methods to further secure media integrity.
Conclusion
Deepfakes are a double-edged sword of modern AI technology – offering creative possibilities while posing serious security risks. The lowered barrier to deepfake creation has democratized the technology, making it accessible to both benign users and malicious actors. As deepfake generation methods continue to evolve, so must our detection and mitigation strategies. It is imperative for organizations and individuals to adopt multi-factor authentication, leverage AI-based detection, and remain vigilant against the potential for deepfake misuse. The fight to maintain the integrity of digital media is ongoing and requires a concerted effort across technology, policy, and public awareness.